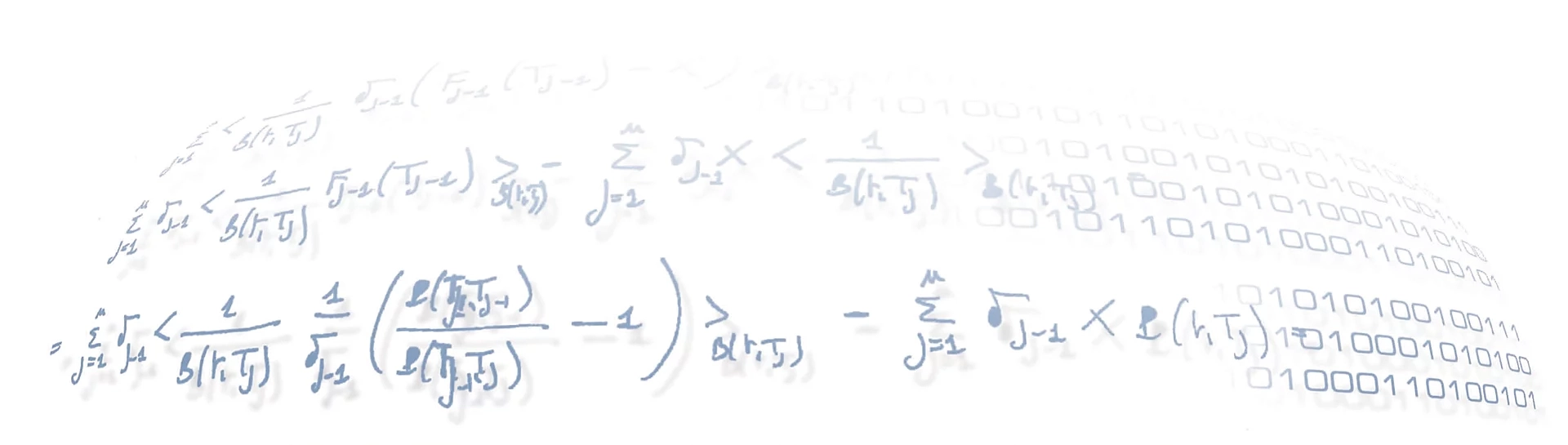
AD — Anomaly Detection

29 January 2021 RecSys for MAD: backtesting resultsRecSys AD |
As a final review of our experiment, we performed a backtesting analysis — sort of, since we are in a non-supervised learning setup. Here we present the main outcomes with an attempt to statistically inspect the resulting top anomalies.
22 January 2021 Universal Anomaly ScoreRecSys AD |
In this post we show some examples of anomaly rank results, highlighting the need for transformation of such values that makes the score interpretable in a universal way, overcoming the specific scale and shape of each RecSys outcome.


15 January 2021 Evaluation of a RecSys as Anomaly DetectorRecSys AD |
Using a RecSys as an anomaly detector undermines the possibility of a supervised-learning approach, so traditional mean average precision metrics are not enough. But even before that, we had to face a fitting convergence evaluation problem.
18 December 2020 Anomaly detection with HTM: an interesting case studyADTS AD |
In this last blog post of the ADTS series we will show an interesting example of anomaly detected on the MTA market data series.

16 December 2020 Anomaly detection with HTM: a real world exampleADTS AD |
In this blog post of the ADTS series we will show an application of an HTM network on a real-time series.
14 December 2020 Anomaly detection with HTM: Anomaly Score and Anomaly LikelihoodADTS AD |
In this blog post we will show how to use an HTM network to solve an anomaly detection problem.


04 November 2020 Hierarchical Temporal Memory (HTM)ADTS AD |
In this blog post we will present a short overview of the Hierarchical Temporal Memory theory.
23 September 2020 Anomaly Detection in Time SeriesADTS AD |
In this blog post series, we will present a real-time anomaly detection tool based on the Hierarchical Temporal Memory (HTM) network. In this first post we will briefly describe the problem of anomaly detection in time series.

21 September 2020 Market Abuse, Recommendation Systems and Anomaly DetectionRecSys AD MA |
As the first thread of our blog, we start with a rather ambitious project: applying Recommendation Systems techniques to create an anomaly detection tool. The approach is quite general, but here we will tell you specifically about our first experiment in the Market Abuse field. In this first post of the series we will briefly describe the terms of the matter.
