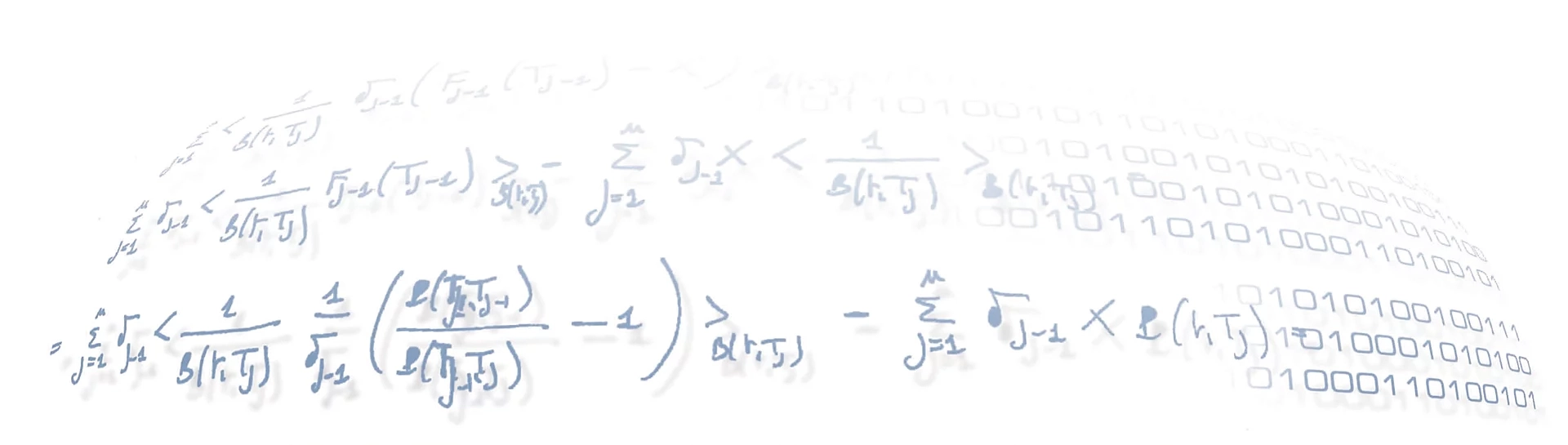



14 February 2022 Market Abuse. Results for the reduction of false positives alarmsRF MA imbalance FP |
In this last post we finally present if the Random Forest trained on the past activity of the compliance officer is able to classify an alarm as false positive or not.
11 February 2022 Market Abuse. Classification with high imbalanced datasetRF MA imbalance |
In this second post of the series, we introduce: the dataset used for the classification problem, the ML approach that better manages the high-imbalanced dataset and finally the statistical metrics used to measure the goodness of the results.

09 February 2022 Market Abuse. Is it possible to reduce false positive alarms?RF MA |
In this series, we explore the possibility to use classical supervised learning techniques to classify alarms generated by a system that implements the Market Abuse Regulation MAR. If successful, this machine learning application could help Compliance Officers to reduce the effort spent in the analysis and classification of the alarms generated.
08 September 2021 Margin Minimization modelMarginOpt CombOpt |
In this second and last episode of the series we will propose a combinatorial optimization model to heuristically solve the margin minimization issue applied to a portfolio of options.


06 July 2021 Portfolio Margin Minimization and Combinatorial OptimizationMarginOpt CombOpt |
In this blog post series, we will present an analysis based on a combinatorial optimization approach to address the problem of margin minimization of an option portfolio. In this first post we will describe in detail the general context in which the problem is inserted and the various techniques which in principle can be used to solve this kind of issues.
12 April 2021 NFK model and LIST Smart OrderOptExec RL |
In this last episode of the series, we will present an extended analysis to test the performance of the NFK model against the LIST Smart Order strategy.


05 April 2021 NFK model and Surrogate Smart OrderOptExec RL |
In this blog post, we will present a preliminary analysis to test the performance of the NFK model against a naive strategy that we have called Surrogate Smart Order.
29 March 2021 The NFK modelOptExec RL |
In this blog post, we will present in detail the characteristics of our reinforcement learning model to approach the optimal execution problem.

22 March 2021 Daily volume profiles and market VWAPsOptExec RL |
Before starting to describe our reinforcement learning model for optimal execution, let us introduce a few elements which might be helpful to better understand some passages of the following posts.
29 January 2021 RecSys for MAD: backtesting resultsRecSys AD |
As a final review of our experiment, we performed a backtesting analysis — sort of, since we are in a non-supervised learning setup. Here we present the main outcomes with an attempt to statistically inspect the resulting top anomalies.


22 January 2021 Universal Anomaly ScoreRecSys AD |
In this post we show some examples of anomaly rank results, highlighting the need for transformation of such values that makes the score interpretable in a universal way, overcoming the specific scale and shape of each RecSys outcome.
15 January 2021 Evaluation of a RecSys as Anomaly DetectorRecSys AD |
Using a RecSys as an anomaly detector undermines the possibility of a supervised-learning approach, so traditional mean average precision metrics are not enough. But even before that, we had to face a fitting convergence evaluation problem.


18 December 2020 Anomaly detection with HTM: an interesting case studyADTS AD |
In this last blog post of the ADTS series we will show an interesting example of anomaly detected on the MTA market data series.
16 December 2020 Anomaly detection with HTM: a real world exampleADTS AD |
In this blog post of the ADTS series we will show an application of an HTM network on a real-time series.

14 December 2020 Anomaly detection with HTM: Anomaly Score and Anomaly LikelihoodADTS AD |
In this blog post we will show how to use an HTM network to solve an anomaly detection problem.
02 December 2020 Evaluation of a RecSysRecSys |
Next steps are tuning the remaining hyperparameters and training the model: but how to establish the soundness and the accuracy of the calibration outcome? The ROC curve, the AOC and the precision/recall at k are the standard metrics aimed at this purpose.


04 November 2020 Hierarchical Temporal Memory (HTM)ADTS AD |
In this blog post we will present a short overview of the Hierarchical Temporal Memory theory.
24 September 2020 RecSys for MAD: an empirical studyRecSys |
In this second episode of the series we'll introduce the ‘real-world’ dataset we've been dealing with. In particular we will discuss the foremost step of the hyperparameter selection phase, namely the mapping we've adopted in order to be able to feed this dataset into a RecSys facility.


23 September 2020 Anomaly Detection in Time SeriesADTS AD |
In this blog post series, we will present a real-time anomaly detection tool based on the Hierarchical Temporal Memory (HTM) network. In this first post we will briefly describe the problem of anomaly detection in time series.
22 September 2020 Optimal Order Execution and Reinforcement LearningOptExec RL |
In this blog post series, we will present an analysis based on a reinforcement learning (RL) technique to address the problem of optimized trade execution in financial markets. We will then compare the performance of our model with the outcomes of the LIST Smart Order strategy.


21 September 2020 Market Abuse, Recommendation Systems and Anomaly DetectionRecSys AD MA |
As the first thread of our blog, we start with a rather ambitious project: applying Recommendation Systems techniques to create an anomaly detection tool. The approach is quite general, but here we will tell you specifically about our first experiment in the Market Abuse field. In this first post of the series we will briefly describe the terms of the matter.
